Identifying Browsers Impacted by WebP Vulnerability with Liongard
IT and cybersecurity professionals face new challenges every day, and today was no exception.
A severe vulnerability in a widely used software module called WebP was announced and patched by Google earlier this month. It was thought to only impact Chrome browsers across Windows, MacOS, and Linux. As of this writing on September 27, further analysis of CVE-2023-4863 has revealed an expansive impact on third-party apps that also utilize the libwebp (version 1.3.2) library.
While vendors have been issuing patches for a few weeks now, the true extent of the vulnerability is only now becoming clear. This particular vulnerability, known as a heap buffer overflow, allows attackers to potentially run malicious code on systems without even being logged in. It is considered one of the most serious types of attacks.
In the coming days, we can expect to see widespread discussions about this issue and critical patches being released for a variety of software applications.
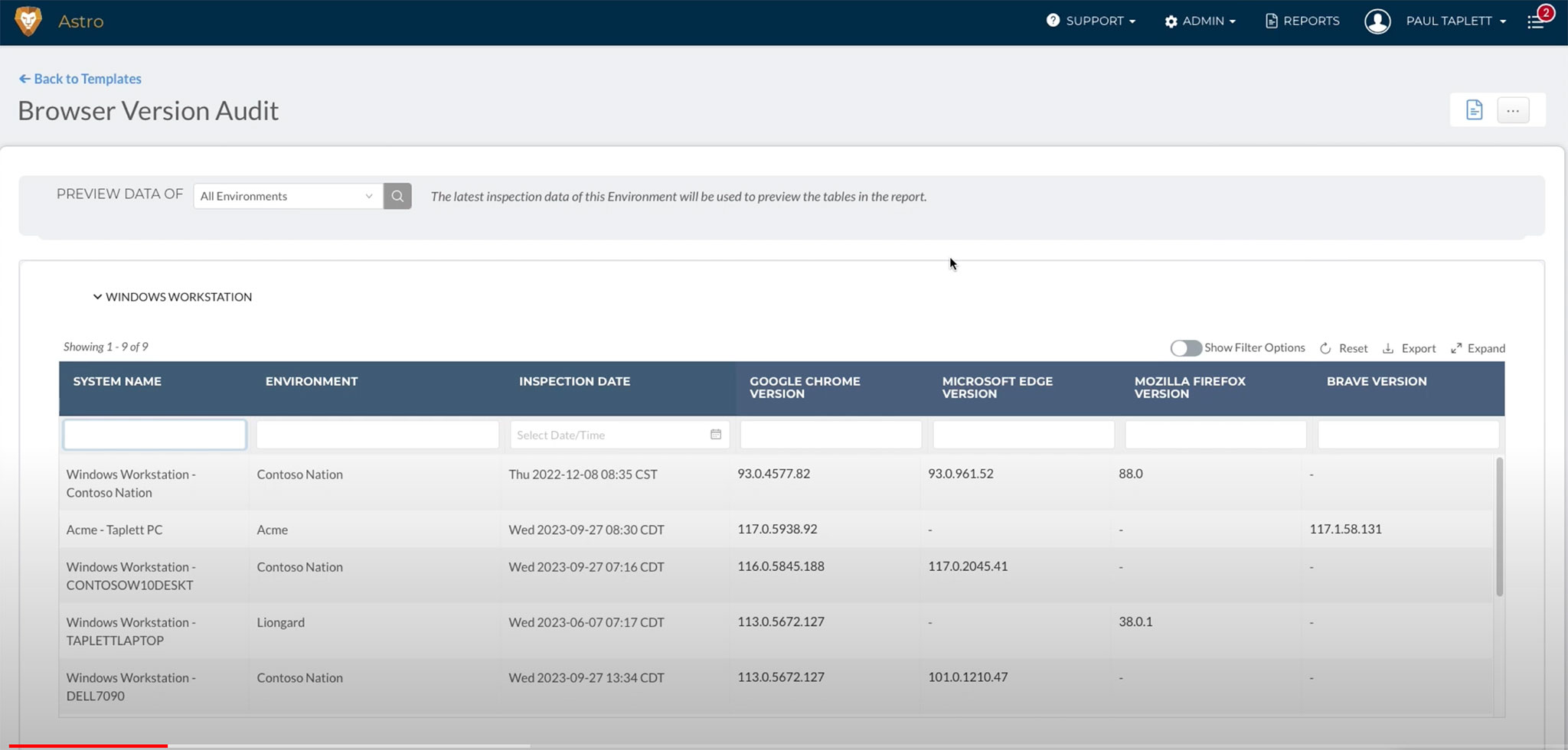
Achieving a fully patched and secure state on customer systems is a significant challenge for IT teams managing multiple systems across different environments. Liongard can assist by conducting quick audits of an MSP’s customer base to identify the installed browser versions. Any unpatched versions can be promptly addressed. To help your team, we have published a video that provides guidance on developing a comprehensive report.
Browsers should be updated to the following versions:
Chrome: Version 116.0.5846.187 (Mac / Linux); version 116.0.5845.187/.188 (Windows)
Firefox: Firefox 117.0.1; Firefox ESR 115.2.1; Thunderbird 115.2.2
Edge: Edge version 116.0.1938.81
Brave: Brave version 1.57.64
The post Identifying Browsers Impacted by WebP Vulnerability with Liongard appeared first on Liongard.